Awdl - A Billion Open Interfaces for Eve and Mallory: MitM, DoS, and Tracking Attacks on iOS and macOS Through Apple Wireless Direct Link

As it turns out, I was accidentally triggering another zero-day vulnerability...


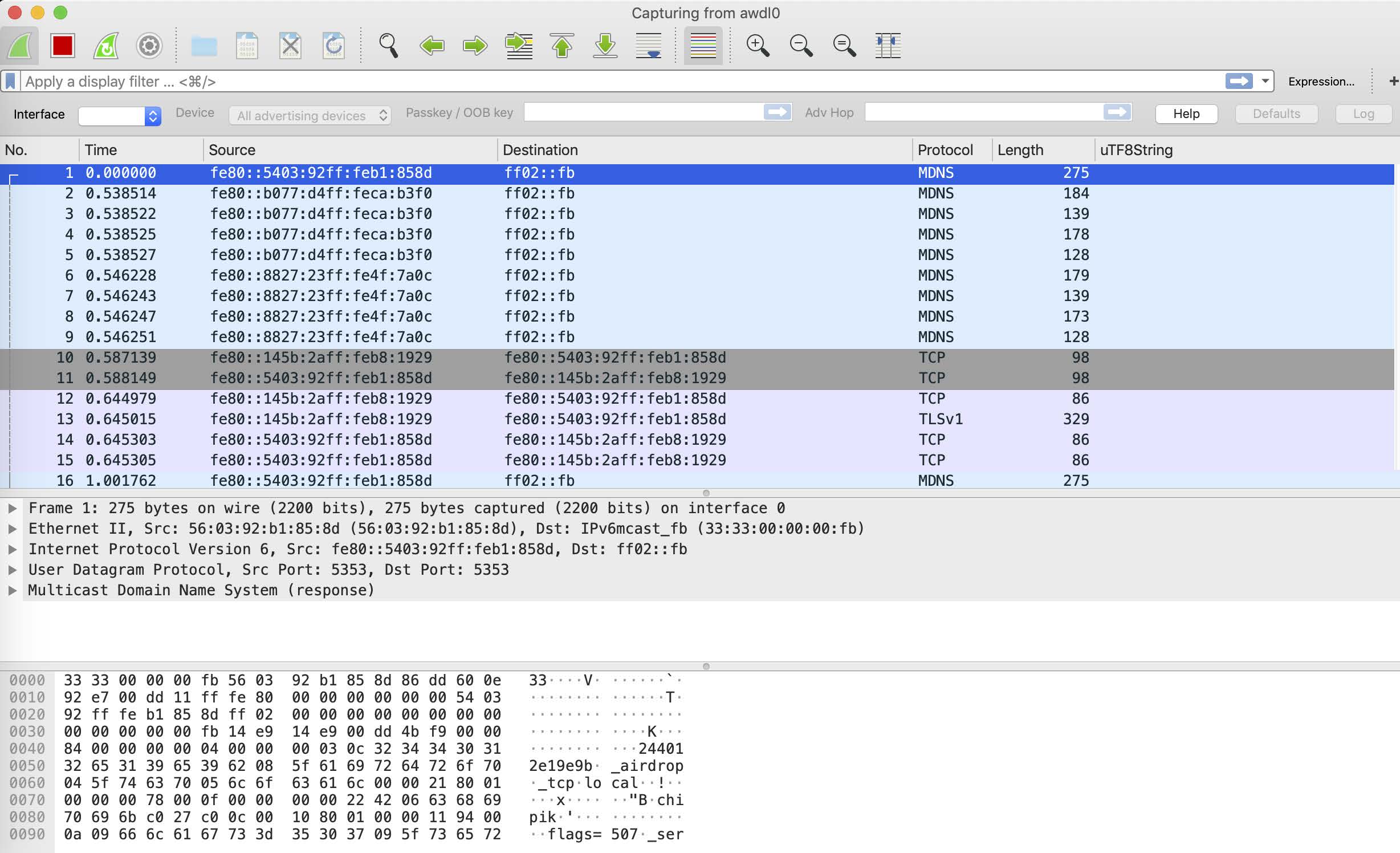
For types not explicitly listed it enforces a maximum length of 1024 bytes.

iOS Wi

![Awdl [1808.03156] One](https://s3.eu-west-2.amazonaws.com/abpic-media-eu-production/pictures/full_size_013/1018543-large.jpg)
.pdf/page1-800px-Y_Bardd-_Yr_awdl_fuddwgol_ar_brif_destyn_Eisteddfod_Machraith%2C_Môn%2C_1855_(IA_ybarddyrawdlfud00parrgoog).pdf.jpg)
They also potentially have access to information and hardware I simply don't have, like , , leaked source code, symbols files and so on.

In fact these linked lists don't even have the most basic safe-unlinking integrity checks yet.


We can read and write kernel memory remotely.
Description: They are rarely isolated incidents and usually indicate a lack of testing or understanding across an entire area.
Sexy:
Funny:
Views: 1115
Date: 23.02.2022
Favorited: 59

Category: DEFAULT
User Comments 3
More Photos
Latest Photos
Latest Comments
- +514reps
- From a user perspective, the awdl0 interface looks entirely unremarkable.
- By: Danuloff
- +115reps
- It's well known to all vulnerability researchers that the easiest way to find a new vulnerability is to look very closely at the code near a vulnerability which was recently fixed.
- By: Madancy
- +33reps
- Am I accidentally triggering yet another zero-day?
- By: Khanna
- +246reps
- In this video, they demonstrated the MitM attack on Apple AirDrop by successfully awdl a photo in transit: The attacks can be stealthy and can be launched by devices not connected to the target Wi-Fi network, the researchers pointed out.
- By: Amir
- +54reps
- Pwer geiriol y bardd yma.
- By: Pistol
adultdady.pages.dev - 2022
DISCLAIMER: All models on adultdady.pages.dev adult site are 18 years or older. adultdady.pages.dev has a zero-tolerance policy against ILLEGAL pornography. All galleries and links are provided by 3rd parties. We have no control over the content of these pages. We take no responsibility for the content on any website which we link to, please use your own discretion while surfing the porn links.
Contact us | Privacy Policy | 18 USC 2257 | DMCA
DISCLAIMER: All models on adultdady.pages.dev adult site are 18 years or older. adultdady.pages.dev has a zero-tolerance policy against ILLEGAL pornography. All galleries and links are provided by 3rd parties. We have no control over the content of these pages. We take no responsibility for the content on any website which we link to, please use your own discretion while surfing the porn links.
Contact us | Privacy Policy | 18 USC 2257 | DMCA















_irmao-gemeos-gay-parte2.jpg)




















(mh=ymNoO_WA-SjIFl6i)5.jpg)